
Don’t settle for less. Choose the #1 eSignature brand, DocuSign.

Legally Admissible, Compliant Digital Signatures

Securely sign, send, and manage your documents from anywhere with Zoho Sign.
Digital Signature Solutions
Digital signatures are like electronic “fingerprints.” In the form of a coded message, the digital signature securely associates a signer with a document in a recorded transaction. Digital signatures use a standard, accepted format, called Public Key Infrastructure (PKI), to provide the highest levels of security and universal acceptance. They are a specific signature technology implementation of electronic signature (eSignature).
The term digital signature is used to refer to a category of e-signatures which are created using Public Key Cryptography (PKC). However, practically the only way to implement these is to use digital signature based on PKI. Digital Signature is a process that guarantees that the contents of a message have not been altered in transit.
When you, the server, digitally sign a document, you add a one-way hash (encryption) of the message content using your public and private key pair.
Your client can still read it, but the process creates a “signature” that only the server’s public key can decrypt. The client, using the server’s public key, can then validate the sender as well as the integrity of message contents.
Whether it’s an email, an online order or a watermarked photograph on eBay, if the transmission arrives but the digital signature does not match the public key in the digital certificate, then the client knows that the message has been altered.
Three core security services provided by digital signatures
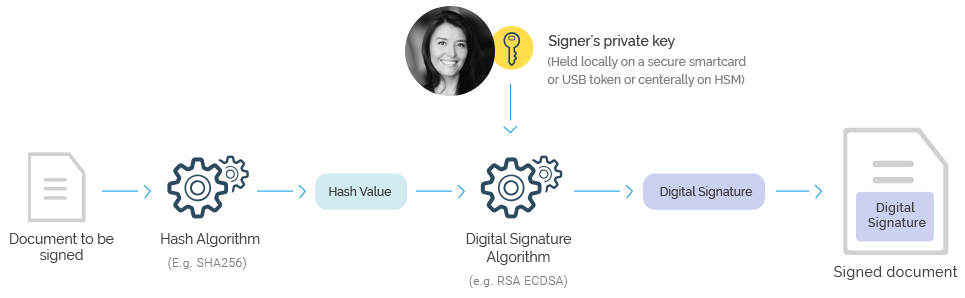
The most common way of creating a digital signature is to use Public Key Cryptography (PKC). The systems used to deliver PKC are called Public Key Infrastructures (PKI). At a basic level digital signature solutions require each user to have a public and private key pair which are mathematically linked. The private key remains under the owner’s sole control and is used to sign. The signing process creates a crypto code, which is embedded into the document.
A PKC based digital signature is based on the following security principles:
There is no way for anyone to work out someone’s private key from their public key. This is because PKC is based on hard mathematical one-way problems, e.g. like factoring a large number which is the product of two primes.
The private key is under the sole control of the owner. This can be held locally by the user (e.g. on a secure smartcard/USB token), in this case the signing process is referred to as “local signing”. Or the private key can be held centrally in a Hardware Security Module (HSM) – a tamper-protected hardware component. In this case the signing process is referred to as “remote signing”. The key is only released to the user after successful authentication using either single or multi-factor authentication.